What is SSH?
SSH is an abbreviation for Secure SHell. Secure is for secure; and what is secure with SSH? The connection to a remote computer. Because SSH is a communication protocol that encrypts the connection between two computers.
A SHell is a user interface Often a console, a command line interpreter (CLI), but it can be a graphical user interface (GUI). Command.com, MS-DOS shell is a CLI shell. Explorer on Windows is a GUI type shell.
SSH will therefore allow us to connect to another computer safely, ie all information (including authentication information. Authentication means that machine B to which A connects must be certain that A is indeed A, and that A must also be sure that it is at B. In other words, A and B ensure that neither of them are usurpers. The data that will circulate between the 2 computers will be encrypted, made unreadable for a possible hacker to listen.

What is an SSH tunnel?
You can use a secure SSH connection to create a tunnel in which the various data that you send and receive with authorized Internet services will circulate. Internet service means everything that is web (http), mail (imap, pop3), ftp, … in fact everything that is TCP. Warning!, Authorized here means that you not only have permission to access these services, but also that the Server Administrator has authorized you to have SSH access to his server.
There are several ways to create an ssh tunnel. We will take the example of a local port transfer to a remote server. The figure below shows the schematic of connecting a local browser to a remote Internet site through an SSH secure tunnel.
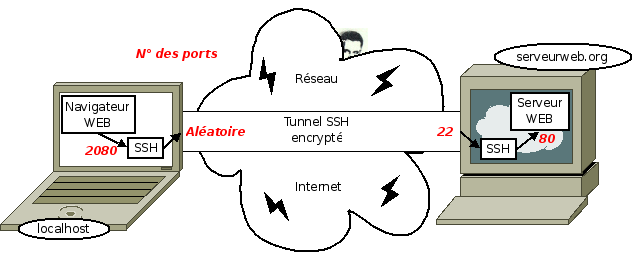
The concept of port
We have noticed in the drawing above, numbers in red bold italic, labeled “N ° of ports”. A computer port is exactly like a door. They are open (pass the data) or closed (or not). There are 2 ^ 16 = 65,536 on a computer. As computer scientists are odd people, the ports are numbered from 0 to 65535.
Ports are also the only way for the computer to know with which application it is doing a chat. There are conventions. By convention, if it is addressed to him on the port 80, the computer will return the request towards the web server. Because it’s like that ;)! The first 1024 ports are, by convention reserved for well-known services, 80 for http, 21 for ftp, 22 for our friend the SSH, etc. These ports numbered from 0 to 1023, in addition, will require to open root rights. The list is here. Other ports are suggested for booking to other less frequent services, if they are not used, you can use these ports. For my example, I use port 2080, if you use Autocad, it may be better to choose another one.
What makes a port open or closed?
It is easy to understand, by analogy with his house, that an open or closed port is a security issue. A port will generally be open or closed:
Client side (here is you), your local firewall or your local router.
Server side, by the server firewall.
How to create an SSH tunnel?
There are 3 approaches:
-L local to redirect a remote port to a local destination (machine)
-R remote (remote) to redirect a local port to a remote destination (machine)
-D dynamic for a dynamic port transfer based on SOCKS (which will facilitate the management of the services of a firewall for server client applications, see, for concrete application, the configuration point of the internet browser in the explanation on putty, or Proxy configuration with GNOME
Note: The page http://projects.tynsoe.org/stm/doc.php, included in the external links gives a good overview of 2 types of SSH redirects, local and remote.





